Case Study on Vulnerability Scanning and Security Reporting
Vulnerability Scanning and Reporting Case Study By Native Expert.
Ph.D. Experts For Best Assistance
Plagiarism Free Content
AI Free Content
Vulnerability Scanning and Reporting
Need assignment help in UK? Native Assignment Help is your ultimate solution. Our seasoned writers possess the expertise to craft impeccable assignments that meet the highest academic standards, guaranteeing your success.
Second part: Vulnerability Scanning and Reporting
A. Brief description of the project
Vulnerability scanning is a process of finding and reporting security vulnerabilities in web applications. It helps the hackers identify the weaknesses in the applications that may lead to security breaches, such as SQL injection attacks or cross-site scripting (XSS) attacks. To perform vulnerability scanning, the hackers need to have a scanner installed on the computer. The most popular scanners are Nessus and OpenVAS, which are used mainly to attack the system or server. Moreover, it can also use Burp Suite for vulnerability testing and penetration testing. A vulnerability scanner will scan the URL of the website by sending it HTTP requests with specially crafted parameters on the system to make the server vulnerable. A description of Nmap and Openvas findings in vulnerability scanning is a report that contains the details of the vulnerabilities discovered by the penetration testing tools. The report has included all the information related to each vulnerability, including its CVSS score, the date and time it was discovered, a description of how it was found, and what action should be taken.
B. Short description of tools and systems
Nmap is a free and open-source tool for network discovery and security auditing. Many systems and networks can be reconfigured to run Nmap, including Windows, Mac OS X, BSD variants, Solaris and many others (Dholey and Shaw, 2019). It was designed by Gordon Lyon of the Nmap Project at Black Hat in 2003. "Nmap" stands for Network Mapper; it was developed as a service to the community that produces the Nmap-service port scanning utility (port listing programme) used by thousands of hackers worldwide.
Openvas is a free and open-source software which can be used to scan the system for vulnerable services, check the operating system version, detect missing patches and address other security issues. It also provides information about installed applications on the machine. Openvas is available in both GUI and command-line interfaces (Abdullah, 2020). The graphical user interface (GUI) allows users to scan all hosts connected to their network with one click.
Figure 1: The useful tools in Kali Linux
NESSUS tool is a new and innovative software solution that allows users to create, manage, and distribute their digital assets. The main purpose of the NESSUS tool is to allow users to get the most out of their content creation by offering them an easy way to manage all the different aspects of their projects. By using this platform, the user will be able to easily organise workflows and collaborate with others for all to share resources (Karayat et al., 2022). This includes managing the content creation process as well as distributing it across various platforms such as social networks or websites.
Metasploitable is a virtual machine that has been created to test the security of the systems. It is based on Ubuntu 8.10 and it comes with an Apache web server, PHP, MySQL and PostgreSQL installed by default. Anyone can use some other software like OpenSSH for secure remote access or BIND DNS Server for DNS service.
CVSS tool is a free web-based application that allows users to generate and manage CVSS scores for their organisation. It provides an easy way to create, store, edit and retrieve CVSS scores in the form of XML files (Theodorus et al. 2021). The tool also helps to import and export CVSS scores from other tools, such as Nessus or NIST's CERT programme.
C. Description of Nmap findings and uses of old versions
Nmap is a free and open source utility for network discovery and security auditing. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed by Gordon Lyon of Internet Security Systems Incorporated (now part of McAfee). The Nmap Project is a non-profit organisation. Nmap is a free and open source (licence) utility for network discovery and security auditing (Samantha and Phanindra, 2018). Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters or firewalls are in use, and dozens of other characteristics. It was designed by Gordon Lyon of Vixie Enterprises for the sole purpose of making the Internet safer by helping to find machines with security holes or misconfigurations that allowed attackers to gain access to sensitive information (Marbun et al. 2020).
Figure 2: Usefulness of Nmap
Nmap is a free, open source vulnerability scanner. It can be used to scan the web application for known vulnerabilities and can also be used as an automated security tool. Namp has a very simple user interface, which makes it easy to use even for people who are not familiar with programming. The main purpose of this tool is to find out if there are any known vulnerabilities on the web application and then fix them before they become exploited by hackers (Samantha and Phanindra, 2018). Nmap scans each page of the website in order to identify all possible vulnerabilities that may exist on it and then fixes them automatically by using its own proprietary tools. Further, the old version of Nmap is a powerful tool that can scan the target network for open ports, and it also provides you with information about the operating system of the hosts in the network. This software is very useful when it comes to finding out whether there are any security holes in the system or not. It also helps to find out which applications are running on different systems. The old software version scans all TCP/IP addresses on a target computer for open ports and version detection (Chhillar and Shrivastava, 2021). Moreover, when an IP address responds to this scan, its port number is displayed along with other details such as OS type, service, and address of the port.
D. Description of Openvas findings
Openvas is a security tool that can be used to scan for and detect vulnerabilities in the operating system. It can also be used to find out which applications are vulnerable. Openvas is not an antivirus application, it does not look for viruses or malware on the computer and it does not provide any protection against them. The main purpose of Openvas is to keep the system safe from potential threats by scanning for known vulnerabilities in the operating system and installed software (Jeremiah, 2019). This is an open source project that aims to provide a simple, easy-to-use and efficient way of creating and running virtualization solutions. Openvas is based on the concept of a virtual machine (VM) where each VM can be configured with different settings. These settings include several tools such as CPU, RAM, storage space, network bandwidth and others. The main goal of Openvas is to allow users to create their VMs in which they can run any operating system or application they want without having to worry about the underlying hardware.
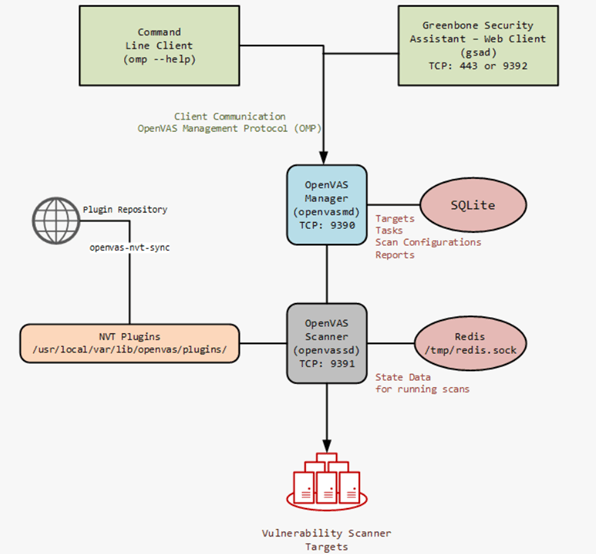
Figure 3: Process of vulnerability scanning in the OpenVAS
The Openvas scanner works on its own without requiring any installation process or configuration steps from an administrator’s order. This can also be used to scan network files such as web server log files and database logs as well as local hard drives or removable media such as USB drives and others. It helps to scan the unknown vulnerabilities by scanning any type of file (for instance, executables, scripts, binaries and others) to make the system stable. Openvas is a free software that helps to detect and remove the malware from the computer. It has been designed to be used as an anti-malware tool for the Windows operating system (Castelo, 2021). In addition to that, it works by scanning the entire system for any malicious files or processes that are running in the background without your permission. Therefore, when it detects any suspicious activity it will display a list of all detected threats along with their for getting permission from the user to remove the vulnerabilities and malicious files to protect the system.
E. Linking findings in Steps C and D with CVE and CVSS Database
Nmap helps to find the open ports of the system whereas Openvas exposes the network vulnerabilities from the network server while utilizing the networks with the help of BurpSuite frameworks. The discussions of Nmap and Openvas have been considered here to find the vulnerabilities in the system and network servers to run the systems and network properly (Kumar et al. 2019). In addition, both pen-testing tools are used for checking the vulnerabilities in the system, where both are free and open-source tools. Further, the Nmap can only find the vulnerabilities by scanning the IP address of the system of the target system whereas Openvas has used the CVE or CVSS database to check the malware or vulnerabilities (Sharmila et al. 2022). Moreover, the CVSS database has been used for web applications to store data that has been provided from the front-end site in XML format. It has been used in the Kali Linux terminal so Openvas has been imported to check the vulnerability of the system. Along with that, CVE-2015-7547 is a vulnerability found in the Linux kernel. It was discovered by Jann Horn of Google Project Zero, who disclosed it to the maintainers of the Linux Kernel on December 21, 2015. The vulnerability allows an attacker to cause a denial of service (DoS) condition or potentially execute arbitrary code as a root user with privileges equivalent to those of the init process.
Vulnerability is defined as any weakness in the design or implementation that makes it easier to exploit a system and gain unauthorized access (Castelo, 2021). Hence, the admin of the database has been maintained through this database for which Openvas has been used. In such cases, the Nmap has been used to scan the port of the database from where the hacker or malicious attackers can attack the database whereas Openvas has been used to find the vulnerability through the overall database. This flaw can be exploited remotely via unprivileged network connections such as Wi-Fi and Bluetooth which can be processed with Opnevas whereas the Nmap tool cannot be used. CVE database has helped to connect with the database of the organisation where it has been accessed through the Kali Linux portal. The vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Ticketmaster. Authentication is required to exploit this vulnerability, and all attacks require user-level privileges (Gilbert and Caudill, 2019). A specific flaw exists within the parsing of HTTP requests by the application, which does not properly validate request parameters. An attacker can leverage this vulnerability to execute code under the context of SYSTEM in order to obtain a local file path that can be used for further exploitation of other vulnerabilities through the same vector or via the database administrators.
CVE database is a collection of security vulnerabilities that are publicly known and can be used to identify the presence of security issues in software. It is maintained by MITRE Corporation, which also maintains the Common Vulnerabilities and Exposures (CVE) project (Kejiou and Bekaroo, 2022). The CVE database contains information on over 1,000 different vulnerabilities found in software products; it is updated daily. Hence, Openvas has to be used for maintaining the databases of the web applications for which Kali Linux has to be used (Deviarinda et al. 2020). It is a vulnerability assessment tool that performs vulnerability scanning and provides the results in an easy-to-understand format. It can be used for penetration testing, network security auditing and compliance testing. Challenges in OpenVisa are a collection of tasks that can be solved by using the OpenVisa tool. The main goal of this project is to improve the quality, reliability and usability of OpenVAS. Each challenge consists of a set of steps that need to be performed on an existing machine with some specific configuration (for instance, operating system version or installed software). It has its requirements and risks, so the hackers need to make sure that the machine meets all the requirements before starting the task.
F. The challenges of vulnerability disclosure
Challenges are a feature of the Vulnerability Disclosure Policy (VDP) that allows for private disclosure to an organisation. The purpose of this is to allow organisations and individuals to disclose vulnerabilities without having their vulnerability disclosed publicly by the vendor or security researcher. This can be useful when there is sensitive information, intellectual property, or other assets at risk in the vulnerability being disclosed. The following types of information may be submitted through challenges that are defined (Dhivvya et al. 2019). These are information on how to reproduce a vulnerability; information on how to exploit a vulnerability; information on how to obtain access credentials; and other information relevant to access credentials without the permission of the users and others.
Challenge is a service provided by the National Cyber Security Centre (NCSC) to help organisations understand their cyber security posture and improve it. The service provides an assessment of the organisation’s current cyber security posture and enables the user to identify areas for improvement. A member of staff will contact the owner directly, or whether they prefer via email, telephone, or in writing, to discuss the organisation’s cyber security needs. They will then carry out a confidential vulnerability assessment on their systems and networks (Chhillar and Shrivastava, 2021). This analysis identifies any weaknesses that could be exploited by malicious actors to gain access to sensitive information or cause.
Conclusion
From the above study, it can be concluded that the penetration test has been processed with the help of Nmap and Openvas toolkits. Further, it can be concluded that it summarizes all findings and actions taken during the test which has been discussed for the organisation to test the confidentiality which has been done by the cyber security. The conclusion should be written in a way that it can be used to reproduce the same result on other systems, or at least provide enough information for someone else to reproduce the findings of the Nmap and Openvas related to CVE and CVSS database. It can be deduced that cyber security has helped to find the vulnerabilities in the system and network server for which several types of hacking tools have been used. Hence, it can be concluded the bank online system has been secured with the help of Nmap, Openvas metasploit and other types of tools where the CVSS database has been used to provide security to the admin and the users as well.
References
Abdullah, H.S., 2020. Evaluation of open-source web application vulnerability scanners. Academic Journal of Nawroz University, 9(1), pp.47-52.
Chhillar, K. and Shrivastava, S., 2021, December. Vulnerability Scanning and Management of University Computer Network. In 2021 10th International Conference on Internet of Everything, Microwave Engineering, Communication and Networks (IEMECON) (pp. 01-06). IEEE.
Deviarinda, J.P., Budiyono, A. and Almaarif, A., 2020. ANALYSIS OF POTENTIAL SECURITY ISSUES IN REGIONAL GOVERNMENT X WEBSITE USING SCANNING METHOD IN KALI LINUX. FoITIC, pp.169-174.
Dhivvya, J.P., Muralidharan, D., Raj, N. and Kumar, B.K., 2019, July. Network simulation and vulnerability assessment tool for an enterprise network. In 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT) (pp. 1-6). IEEE.
Dholey, P. and Shaw, A.K., 2019. OnlineKALI: Online vulnerability scanner. In Proceedings of International Ethical Hacking Conference 2018 (pp. 25-35). Springer, Singapore.
do Castelo, V., 2021, June. A Performance Assessment of Free-to-Use Vulnerability Scanners-Revisited. In ICT Systems Security and Privacy Protection: 36th IFIP TC 11 International Conference, SEC 2021, Oslo, Norway, June 22–24, 2021, Proceedings (Vol. 625, p. 53). Springer Nature.
Gilbert, K. and Caudill, B., 2019. Hands-on Aws penetration testing with Kali Linux: set up a virtual lab and pentest major Aws services, including EC2, S3, Lambda, and CloudFormation. Packt Publishing Ltd.
Jeremiah, J., 2019, September. Intrusion detection system to enhance network security using raspberry pi honeypot in kali linux. In 2019 International Conference on Cybersecurity (ICoCSec) (pp. 91-95). IEEE.
Karayat, R., Jadhav, M., Kondaka, L.S. and Nambiar, A., 2022, March. Web Application Penetration Testing & Patch Development Using Kali Linux. In 2022 8th International Conference on Advanced Computing and Communication Systems (ICACCS) (Vol. 1, pp. 1392-1397). IEEE.
Kejiou, A. and Bekaroo, G., 2022, October. A review and comparative analysis of vulnerability scanning tools for wireless LANs. In 2022 3rd International Conference on Next Generation Computing Applications (NextComp) (pp. 1-6). IEEE.
Kumar, B.K., Raj, N., Dhivvya, J.P. and Muralidharan, D., 2019, April. Fixing network security vulnerabilities in local area network. In 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI) (pp. 1349-1354). IEEE.
Marbun, P.A., Almaarif, A. and Budiono, A., 2020. Website Security Analysis of Department and Integrated Services One Door of XYZ Regency using Kali Linux.
Samantha, B.S. and Phanindra, M.V., 2018. An Overview on the Utilization of Kali Linux Tools. International Journal of Research and Analytical Reviews, 5(2).
Sharmila, C., Gopalakrishnan, J., Shanmuga Prasath, P. and Daniel, Y., 2022. Multipurpose Linux Tool for Wi-Fi Based Attack, Information Gathering and Web Vulnerability Scanning Automations. In International Conference on Image Processing and Capsule Networks (pp. 587-598). Springer, Cham.
Theodorus, D., Nabi, M.S. and Al-Maatouk, Q., 2021, October. Web-based Reconnaissance and Vulnerability Scanner: A Review and Proposed Solution. In 2021 International Conference on Data Analytics for Business and Industry (ICDABI) (pp. 666-670). IEEE.
Go Through the Best and FREE Case Studies Written by Our Academic Experts!
Native Assignment Help. (2026). Retrieved from:
https://www.nativeassignmenthelp.co.uk/vulnerability-scanning-and-reporting-case-study-19382
Native Assignment Help, (2026),
https://www.nativeassignmenthelp.co.uk/vulnerability-scanning-and-reporting-case-study-19382
Native Assignment Help (2026) [Online]. Retrieved from:
https://www.nativeassignmenthelp.co.uk/vulnerability-scanning-and-reporting-case-study-19382
Native Assignment Help. (Native Assignment Help, 2026)
https://www.nativeassignmenthelp.co.uk/vulnerability-scanning-and-reporting-case-study-19382
- FreeDownload - 1502 TimesCase Study On Bipolar Disorder
Introduction - Case Study On Bipolar Disorder Psychological disorders are...View or download
- FreeDownload - 850 TimesSTO306HK - Current Issues in Management Maxims Group
STO306HK - Current Issues in Management Maxims Group Case Study Current Issues...View or download
- FreeDownload - 623 TimesMitchells & Butlers Marketing Mix: Strategies for Hospitality Success Case Study
How M&B Combines Innovation and Marketing in the Hospitality...View or download
- FreeDownload - 1533 TimesBritish Airways Strategy: Maximize Market Edge Case Study
Introduction - BA's Competitive Growth: Strategic Analysis Understanding and...View or download
- FreeDownload - 1276 TimesInternational Business Ben & Jerry's Case Study
International Business Ben & Jerry’s Case Study Introduction...View or download
- FreeDownload - 1638 TimesUnit 2 Marketing essential coca-cola case study
Unit 2 Marketing essential coca-cola case study Get free samples written by...View or download
-
100% Confidential
Your personal details and order information are kept completely private with our strict confidentiality policy.
-
On-Time Delivery
Receive your assignment exactly within the promised deadline—no delays, ever.
-
Native British Writers
Get your work crafted by highly-skilled native UK writers with strong academic expertise.
-
A+ Quality Assignments
We deliver top-notch, well-researched, and perfectly structured assignments to help you secure the highest grades.