Question 1
Introduction:Customer Due Diligence - Key to Fighting Financial Crime
Assessing and mitigating risks from financial crimes is never complete without Customer Due Diligence (CDD). It pertains to gathering, and analyzing information to ensure transparency and prevent financial systems misuse for activities of money laundering, terrorist financing and human trafficking. Towards rebuilding its reputation following recent scandals ICT Bank is crucial for strengthening CDD not only to comply with regulatory exigencies but to clear its name. With the application of effective CDD measures, the bank will return customers' trust, refurbish its systems and show to whom it is battling the fight against financial crime.
If you need assistance understanding complex AML topics like Customer Due Diligence and risk-based approaches, our expert assignment help service covers ICA Advanced Certificate in AML comprehensively. From regulatory frameworks to practical challenges, our tutors deliver quality guidance to boost your academic performance effectively. Seek assignment help now!
Explanation of Customer Due Diligence
Definition of Customer Due Diligence (CDD)
Customer Due Diligence (CDD) is the process by which a financial institution gathers, verifies, and monitors information about a customer for risk of money laundering or other related crimes. First and foremost, the adverse use of financial systems is prevented through general Anti-Money Laundering (AML) compliance which is a basic aspect of it (Chitimira and Munedzi, 2023). CDD is the process whereby organizations know who their customers are, the nature of their business and the legitimacy of the transactions.
Key Components of CDD
Identification, verification and understanding of customer activity in CDD is the primary. Identification includes collecting customer basic information such as name, date of birth and address. Validation of this information means you will need to city yourself therefore verifiable by government-issued ID or utility bills.
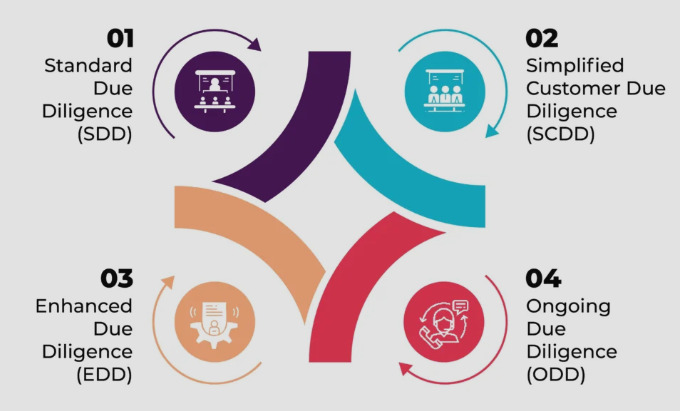
Figure 1: CDD Measures Type
(Source: Chitimira and Munedzi, 2023)
To understand customer activity, an assessment of the purpose of the relationship, expected transaction patterns and any unusual or suspicious behaviour, is necessary. They are essential to building out a risk profile for each customer such that the best possible measure can be applied where it's needed.
Regulatory Framework
The application of CDD is governed by the Money Laundering, Terrorist financing, and Transfer of Funds (Information on the Payer) Regulations 2017 (MLRs 2017), in the United Kingdom. Specifically, it defines the circumstances when financial institutions shall conduct CDD at onboarding of a customer, suspicious activity, or high-risk transaction. ICT Bank could be fined $85 million for failing to meet these requirements and the penalties for failing them are severe (Update, 2023).
Examples of CDD in Practice
CDD is most often used during customer onboarding when institutions get and verify important information before developing a business relationship with that customer. Another part of a critical piece of ensuring that customer activities are consistent with their known risk profile is ongoing monitoring — enabling institutions to monitor customer activities continually (George et al., 2022). For example, enhancing ICT Bank's commitment in terms of providing enhanced transaction monitoring is an indication of the importance of robust CDD processes in curtailing its financial crime risk.
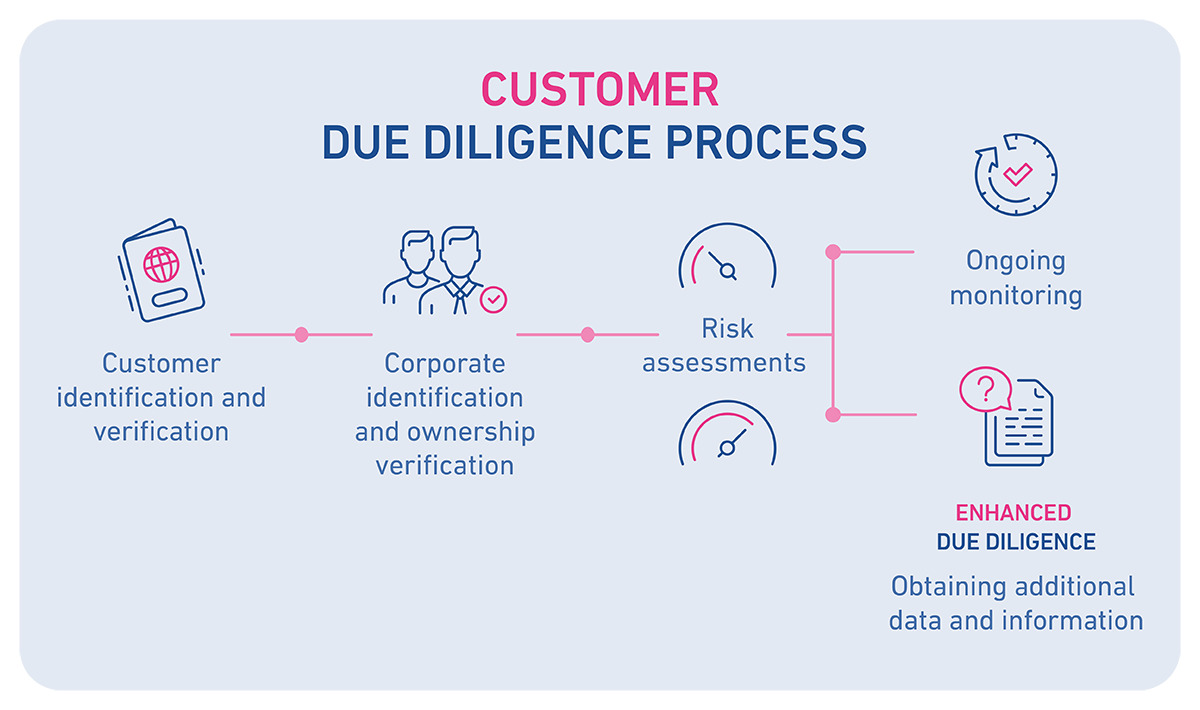
Figure 2: CDD Process
(Source: George et al., 2022)
Practicalities and Challenges of Applying a Risk-Based Approach to CDD
Risk-Based Approach (RBA)
RBA provides financial institutions with a risk-based approach (RBA) of Customer Due Diligence (CDD) enabling a more efficient allocation of resources based on the customers and the transactions that pose the highest risk of money laundering or financial crime. The first approach is to profile risk (customers are rated on their geographic location, nature of business, transaction patterns, and political exposure). Among other things, we help institutions distinguish between customers that fall into the low, medium and high-risk buckets, thus allowing the institutions to specify the degree of scrutiny each of their business relationships needs (Tucker, 2024). Enhanced Due Diligence (EDD) is required for high-risk customers: for instance, Politically Exposed Persons (PEPs) or entities from high-risk jurisdictions (as a consequence of high risks).
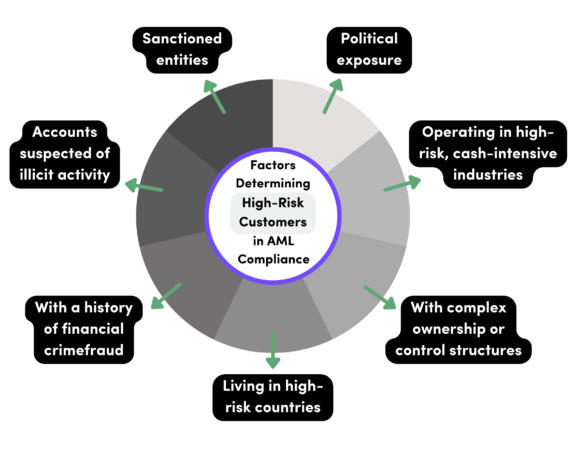
Figure 3: Risk-Based Approach to AML
(Source: Tucker, 2024)
The RBA is about resource allocation. Compliance efforts for institutions are concentrated in areas, such as high-value transactions and customers who have complex corporate structures, where they are at risk. The result is a targeted approach: while this approach limits the enforcement of anti-money laundering policies to only those that might legitimately raise suspicion, it preserves operational efficiency by minimizing attention to low-risk customers.
Challenges in Applying RBA
Identifying high-risk customers is one of the main challenges in implementing an RBA. To do this, you need to have access to trustworthy data and screening tools, including PEP databases and sanctioned entity databases. Meanwhile, incomplete or outdated data will hinder effective profile risk and leave gaps in compliance. Another major problem is balancing compliance costs with operational efficiency (Wilson et al., 2011). High-risk customers need high-risk due diligence and that means significant resources in people and automation. Because these requirements can be resource-intensive, small or resource constricted the institutions may face difficulty meeting these requirements, leaving them vulnerable to the AML framework.
RBA implementation is also complicated by technology and data quality issues. Because legacy systems often don't have the sophistication to provide comprehensive monitoring, new technologies such as AI-driven anomaly detection can be expensive and time-consuming. Poor data quality can undermine risk assessments — records that are inconsistent or where there is no customer history, for instance.
Examples of Challenges
RBA addresses the complexities in the unique field of managing cross-border risks. Since customers operate in multiple jurisdictions, their risk profiles can be somewhat different, and this can be hard to assess. Even more problematic is the offshore account, infamous for being a device for secrecy and anonymity, making the tracking of fund origination and destination that much harder.
For instance, weak ICT Bank controls in dealing with cross-boundary risks lead to regulatory penalties against it. Money laundering vulnerabilities remain a problem and underscore the need for robust systems, together with international collaboration to combat these, using offshore accounts. In responding to these problems, financial institutions will be better prepared to strengthen their RBA frameworks and generally improve their overall AML compliance.
Ensuring the Effectiveness of CDD Processes
Key Measures to Enhance Effectiveness
To improve the effectiveness of Customer Due Diligence (CDD) processes, targeted measures are needed to address high-risk scenarios and to improve the overall system efficiency. For customers with a high-risk profile such as PEPs or businesses in high-risk jurisdictions, an important step in combating financial crime is Enhanced Due Diligence (EDD). EDD will review customer activities in detail: source of funds verification and additional checks on the transactions (Matthews, 2022). This allows risks with such customers to be identified and controlled appropriately.
CDD processes critically rely on technology to improve their overall efficiency and accuracy. However advanced tools such as artificial intelligence (AI) or machine learning allow institutions to see patterns and anomalies live.
Measuring Effectiveness
The process of CDD is required to be timely and further tests are required. Internal reviews help to fill the gaps in compliance and have actionable insights. External audits, however, guarantee alignment with regulatory expectations and best practices. Customer feedback also gives a different view: where CDD processes introduce unnecessary friction or fail to meet customer needs. Additional benchmarks for effectiveness are the regulatory reviews (Mugarura, 2014). Findings of regulatory assessments can be determined as the ways institutions can evaluate the compliance level and they can address the recommended changes. Providing CDD frameworks with a proactive approach to regulatory feedback is a way of building trust with authorities, but also strengthens them.
Examples of Best Practices
An effective CDD process fully embraces collaboration with the regulators. It also provides institutions with an opportunity to communicate with the institution and provide it with information regarding evolving risks and regulatory expectations. The use of advanced data analytics tools as a best practice, however, additionally contributes to the improvement of risk assessment. For example, predictive analytics can help to predict the emergence of risks that might compromise institutions' CDD strategy and allow for proactivity in the institutions' adoption of the CDD strategy. ICT Bank can restore its dismantled reputation and can be made more efficient in the fight against financial crime by integrating these measures.
Recommendations and Conclusion
Customer Due Diligence (CDD) is critical both as a means of combating financial crime and to restore the reputation of ICT Bank. CDD can be effective if it is carried out through accurate identification of customers, use of risk-based approaches and continuous monitoring. Similarly, proactive challenges have to be faced in the areas of managing cross-border risks and using technology. ICT Bank needs to prioritize doing Enhanced Due Diligence on high-risk customers, embrace advanced technologies such as AI in anomaly detection and improve staff training programs, all to strengthen ICT Bank's processes. To restore customer trust and become a sustainable and leading CDD processing partner, Robust CDD processes are critical. If proper recommendations by ICT Bank are implemented, the Bank can position itself as a leader in AML compliance.
Question 2
Introduction
In this regard, an AML first-line defence employee must make a distinction between 'knowledge,' 'suspicion,' and 'reasonable grounds to suspect' in the identification and reporting of suspected financial crimes. To that effect, it's clear that if such differences are known, every prospect of excess or false reporting comply with legal obligations under the Proceeds of Crime Act 2002 in the UK. In addition to these, other important components of a robust AML framework include an effective internal reporting system along with requirements for submitting SARs or STRs to the authorities.
The differences between knowledge, suspicion, and prima facie case for suspecting
- Acquisition
Definition: Actual evidence of criminal activity, such as direct proof of money laundering or fraud.
Examples: Obtaining counterfeit documents or getting a direct confession of illegal activity from a customer.
Legal Dimension: POCA considers it an offense to fail to report one's knowledge on money laundering.
- Suspicion
Definition: a sensation or opinion that something is wrong, contrary to definite indicators, even in the absence of concrete evidence.
Examples: Unusual account activity, such as frequent large deposits inconsistent with a customer's profile.
Problems: Managing subjective judgment by submitting unnecessary SARs.
Relevance: Suspicion is sufficient to trigger reporting obligations under UK law.
- Probable Cause to Suspect
Definition: An objective test where a reasonable person with the same information would have grounds to suspect money laundering.
Examples: Transactions with high-risk jurisdictions or unexplained wealth that are inconsistent with declared income.
UK Standards Reasonable grounds to suspect require financial institutions to act regardless of the subjective feelings of its staff members.
Key elements of a good internal reporting system
- Clear Reporting Channels
Employees should also be educated to identify suspicious activity and report it to the Money Laundering Reporting Officer (Al Asmri, 2022). The predefined procedures ensure that concerns are dealt with fast and systematically.
- Privacy and Safety
Whistleblower protections protect staff from retaliation for reporting issues. Secure systems safeguard sensitive information related to reports.
- Monitoring and Oversight
Regular internal audits evaluate the system’s effectiveness. It is through technology transaction monitoring software that identifies and escalates abnormal patterns. Specifications of SAR/STR Submissions in the UK
SAR/STR in the UK
- Timing and Content
Under POCA, the authority has required the submittance of SARs when suspicion arises. There must be key information in the reports on the customer, the transaction detail, and why there is suspicion (Gowhor, 2022). More, for example, a SAR on unexplained high-value deposits would indicate how the declared income differed from the account activity.
- Contact with bureaucracy
SARs in the UK are directly submitted through the secure online portal of the National Crime Agency (NCA). In some cases, however, before proceeding to further process a transaction connected with suspicious activity, there needs to be a "request for consent." This protects the financial institution from any liability but gives law enforcement the opportunity to act.
- Compliance and Maintenance
The Money Laundering Regulations 2017 require financial institutions to keep copies of SARs and related documentation for at least five years.
Recommendation & Conclusion
By ending this distinction between 'knowledge', 'suspicion,' and 'reasonable grounds to suspect' is significant toward ensuring only genuine threats are reported and the AML efforts are bolstered. With an effective internal reporting system and SAR/STR submission compliance, these details help the financial institution play a vital role in fighting financial crime. An improvement in the reporting framework of ICT Bank would be a vital step in the reconstruction process and towards achieving adherence to AML regulations.
Question 3
Introduction
Cryptocurrency, owing to its anonymous characteristic and ease of accessibility and efficiency as a medium of exchange throughout the world, has attracted widespread adoption. These hallmarks make it more vulnerable than any other form of money to ML. The regulation of cryptocurrencies in the UK is governed by the Money Laundering, Terrorist Financing, and Transfer of Funds (Information on the Payer) Regulations 2017, also known as MLRs 2017. This report explores vulnerabilities in cryptocurrency to ML risk factors and mitigating measures.
Vulnerabilities of Cryptocurrency to Money Laundering
- Anonymity and Pseudonymity
Cryptocurrencies like Bitcoin operate on blockchain technology, where transactions are pseudonymous. Although public, blockchain data does not reveal the true identity of participants, making it difficult to trace illicit activities. Using this characteristic, criminals hide the layers of how illegal financial proceeds originated.
- Facilitation of Cross-Border Transactions
It involves decentralized and borderless transactions in relation to cryptocurrencies, thus perhaps extremely convenient for cross-border money laundering. For example, a money launderer can transfer large amounts at the speed of light across jurisdictions with little oversight from regulators or financial institutions.
- Lack of Regulation
Laws in some jurisdictions regarding AML are poor or inconsistent for cryptocurrencies. Exchanges from risky or poorly regulated countries may expose vulnerabilities when transactions related to cryptocurrencies are involved.
- Privacy Coins and Mixing Services
Privacy coins like Monero and Dash provide additional anonymity features, further concealing transactions (Johari et al., 2020). Mixers or tumblers, which separate and recombine cryptocurrency, add even more layers of obfuscation by making it not much easier to trace a source of funds.
Risk Mitigation Measures
- Legal Compliance
Cryptocurrency exchange and wallet companies in the UK fall under MLRs 2017, encompassing CDD and Enhanced Due Diligence when dealing with higher-risk transactions. For example, exchanges must verify customer identities and monitor transactions for suspicious activities.
- Transaction Monitoring
Advanced technologies, such as blockchain analytics tools, can detect suspicious activities. For example, sites like Chainalysis and Elliptic exist through which connections between wallet addresses and known criminal entities become evident.
- Training and Learning
The banking and crypto firms should, therefore, educate their employees on how to identify typologies of cryptocurrency, such as use of privacy-enhancing technologies or anomalous transaction volumes.
With institutions like the Financial Conduct Authority (FCA) and the National Crime Agency (NCA) help to strengthen the AML efforts (Rysin and Rysin, 2020). Information-sharing initiatives, for example, Joint Money Laundering Intelligence Taskforce (JMLIT), assist in identifying the risks appearing in cryptocurrency transactions.
Conclusion
Anonymity, cross-border transactions, and dearth of a legal framework in some jurisdictions raise specific challenges for AML compliance in cryptocurrency. Conversely, regulatory compliance, including transaction monitoring and engagement with authorities, is a cure to such risks. For ICT Bank, blockchain analytics and robust CDD for cryptocurrency transactions are something that will take it one step forward in the preventive measures against financial crimes and the strengthening of AML measures in this emerging sector.
References
Journals
Chitimira, H. and Munedzi, S., 2023. An evaluation of customer due diligence and related anti-money laundering measures in the United Kingdom. Journal of Money Laundering Control, 26(7), pp.127-137.
George, S., Hunter, T. and Thind, R., 2022. FINANCIAL CRIME AND ENFORCEMENT AGAINST PAYMENTS FIRMS AND PAYMENTS SYSTEMS. In Payment Services (pp. 128-182). Edward Elgar Publishing.
Matthews, B., 2022. The need for customer due diligence to adapt to the digital era. Journal of Digital Banking, 7(1), pp.37-45.
Mugarura, N., 2014. Customer due diligence (CDD) mandate and the propensity of its application as a global AML paradigm. Journal of Money Laundering Control, 17(1), pp.76-95.
Tucker, O., 2024. Risk-based customer due diligence is the key to effectively managing financial crime risk. Journal of Financial Compliance, 8(1), pp.65-79.
Update, A.S., 2023. 2023.
Wilson, D.M., Rowley, P.N. and Watson, S.J., 2011. Utilizing a risk-based systems approach in the due diligence process for renewable energy generation. IEEE Systems Journal, 5(2), pp.223-232.
Gowhor, H.S., 2022. The existing financial intelligence tools and their limitations in early detection of terrorist financing activities. Journal of Money Laundering Control, 25(4), pp.843-863.
MANUAL, G., LEGAL PERSONS AND ARRANGEMENTS ML RISK ASSESSMENT TOOL.
Al Asmri, M., 2022. The experience of UK medical/physician associate students in the acquisition of intimate physical examination skills, and the role of technology-enhanced simulators in facilitating learning (Doctoral dissertation, University of Birmingham).
Rysin, V. and Rysin, M., 2020. The money laundering risk and regulatory challenges for cryptocurrency markets. Restructuring management models-changes-development, pp.187-201.
Johari, R.J., Zul, N.B., Talib, N. and Hussin, S.A.H.S., 2020, March. Money laundering: Customer due diligence in the era of cryptocurrencies. In 1st International Conference on Accounting, Management and Entrepreneurship (ICAMER 2019) (pp. 130-135). Atlantis Press.
Leuprecht, C., Jenkins, C. and Hamilton, R., 2023. Virtual money laundering: policy implications of the proliferation in the illicit use of cryptocurrency. Journal of Financial Crime, 30(4), pp.1036-1054.