Ethical Hacking
Introduction
With the increase in the size of cyberspace, the crime rate related to cybercrimes is increasing day by day; that is why ethical hacking and digital forensic programmes are needed. Ethical hacking is the process of emulating attacks on the targeted systems with the intention of exposing their weak points before the black hats can exploit them, and the process involves White Box, Grey Black and Box methodologies. The Red Team here acts like the ways in which an intruder will attack while the Blue team will be using intrusion detection as well as the use of encryption. Security is served with the help of patching vulnerability, for example, ransomware problems which can endanger the systems. Digital computer crime is the study of various crimes that transpire in cyberspace through data collection duplication and validation using tools such as Autopsy, Nmap and FTK Imager. The general integration of ethical hacking and forensic in an organization enhances the security of a computer system and prevents incidents to grow while containing them.
Activity 2.1: Penetration Testing Boxes
Task: Research on the three penetration testing techniques: White box, Grey Box, and Black Box. In this paper there is a need to elaborate on the distinctions between these ‘boxes’ and give examples for each.
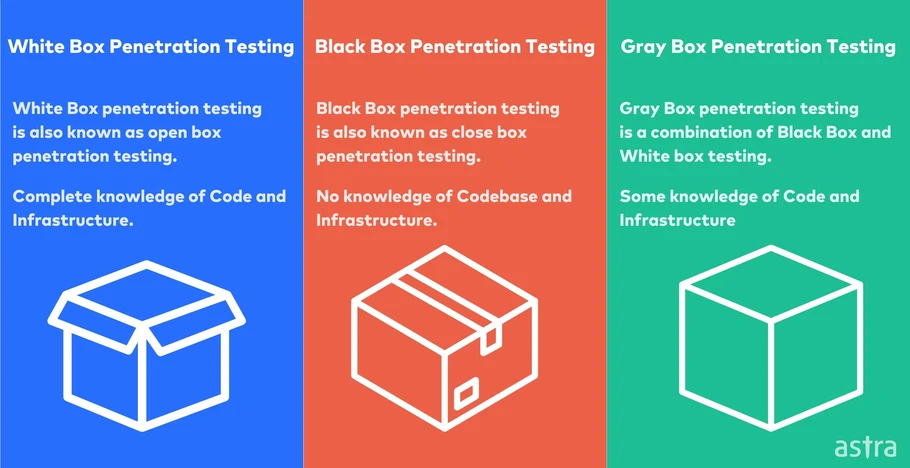
Figure 1 : Penetration Testing Boxes
(Source : https://www.getastra.com/blog/security-audit/white-box-penetration-testing/)
Solution:
White Box Testing
White Box Testing is also referred to as Clear Box or Internal Testing under which the tester has full insight into the formation of a network, codes, and settings. It draws a clear understanding of weaknesses that are not easily recognized from outside as a layman (Baddam et al., 2020). This is used to gain information on how the system can be protected through assessing the design, code, as well as the configuration.
Example: A company’s IT department brings in an experienced tester with privilege level on routers, firewalls, and servers in order to identify configuration blunders and code cracks.
Grey Box Testing
By definition, Grey Box Testing is an intermediate of White Box Testing and Black Box Testing. The tester has not much experience in testing the system and has a limited knowledge of documentation, network, and users (Devi et al., 2020). This procedure is close to an insider attack method in which the tester has to find out unknown weaknesses himself/herself.For instance, a penetration tester having employee privileges but limited physical or IT administrative access tries to uncover insider threats.
Black Box Testing
Black Box Testing is also regarded as the most effective since the tester does not have previous knowledge on the system. The goal is to understand which assets can weaken a malicious user, who tries to enter an organization’s environment through open doors, i.e., through interfaces connected to the internet including websites or APIs.
Example: A tester attempts to have unauthorized access to a corporate web site given only the web address without having the system map of the organization.
Conclusion
As stated, there are certain advantages of each of the testing methodologies. White Box is detailed and takes a lot of time, Grey Box is focused on internal and external view, and Black Box checks the strength of the system in the real external conditions.
Reference List
Baddam, P.R., 2020. Cyber Sentinel Chronicles: Navigating Ethical Hacking's Role in Fortifying Digital Security. Asian Journal of Humanity, Art and Literature, 7(2), pp.147-158.
Devi, R.S. and Kumar, M.M., 2020, June. Testing for security weakness of web applications using ethical hacking. In 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI)(48184) (pp. 354-361). IEEE.
Activity 2.2: Red Team vs Blue Team
Solution:
Red Team (Offensive Security)
It is important to note that the Red Team is the one that conducts the imitation of cyberattacks on the university’s online services in order to discover the vulnerabilities.
Steps for Attack:
- Intelligence Gathering : Gathering information on the university’s email servers, file-sharing systems, and web servers using OSINT and other tools which include Nmap.
- Gaining access : The team tries to take advantage of a hole, for example in the SQL injection, cross-site scripting (XSS) or unpatched code.
- Gaining Privileges : After that, the team then gains higher privilege just to review and access more sensitive data or manage systems.
- Persistence : The attackers ensure that they maintain an interface that allows them to continue controlling the computer even after getting detected.
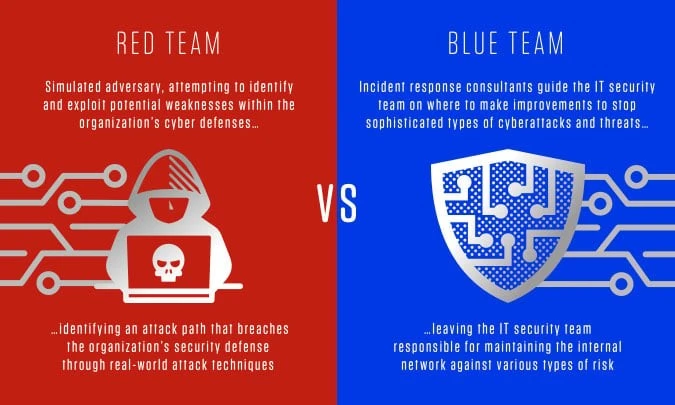
Figure 2: Red Team vs. Blue Team
(Source : crowdstrike.com/en-us/cybersecurity-101/advisory-services/)
This is done by putting into place a set of security controls and then counteracting threats as they are being launched by the Red Team.
Defensive Strategies:
- Surveillance: The team uses IDSs and IPSs to identify miscreants’ malice in the network.
- Patching: Ensuring that all programs and applications in the system implement all the latest security patches to prevent exploitation of the same for instance in accessing unauthorized data.
- Incident Response: After detecting an incident, it is followed by developing a proper plan to contain the infected systems (Conteh et al., 2021)., which involve a proper procedure to analyse the breach and control the threats.
- Security: enhancement of the protective measures that would involve MFA, data encryption, as well as the RwU data access control mechanisms.
Both of them are very important in cyber defense though the Red Team identifies vulnerabilities while the Blue Team tries to improve on the security of the systems in order to minimize the chances of an attack.
Reference List
Conteh, N.Y. and Schmick, P.J., 2021. Cybersecurity risks, vulnerabilities, and countermeasures to prevent social engineering attacks. In Ethical hacking techniques and countermeasures for cybercrime prevention (pp. 19-31). IGI Global.
Activity 2.3: Software Patches
Solution:
Software Patching and Updates
Software patching refers to the process of applying an update to existing applications for a purpose of resolving the development shortcomings, increasing product capabilities, and safety measures (Christen et al., 2020). Patches contain solutions to vulnerabilities made by developers in the system or by security experts in order to avoid exploitation.
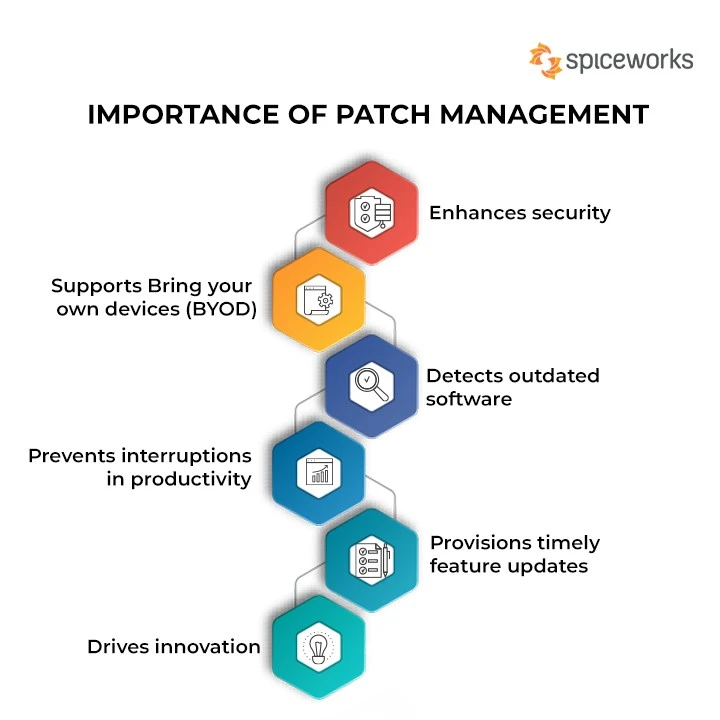
Figure 3: Software Patches
(Source : https://www.spiceworks.com/tech/devops/articles/what-is-patch-management/)
Security Risks of Outdated Software:
- Exploits : The other one is that attackers can take advantage of any vulnerability that the developers have not patched, making it possible to gain unauthorized access or breach the system.
- Malware : This means that systems that have not been patched are vulnerable to ransomware attacks such as the WannaCry attack.
- Denial of Service (DoS) : This is another form of attack whereby the attacker exploits the existing unpatched vulnerability to deny service.
Solution for Legacy Systems:
- Mitigations : Firewall and segregate the network; monitor the network and systems.
- Virtual Patching : WAFs and intrusion prevention systems can be used to handle the threats.
Conclusion:
One area that cannot be ignored is regularly operating system patching because of the rampant cyber threats. It means if updates are not available for the legacy systems, the organizations must employ other additional measures in order to secure their data.
Reference list
Christen, M., Gordijn, B. and Loi, M., 2020. The ethics of cybersecurity (p. 384). Springer Nature.
Activity 2.4: Pre-test Activity
Solution:
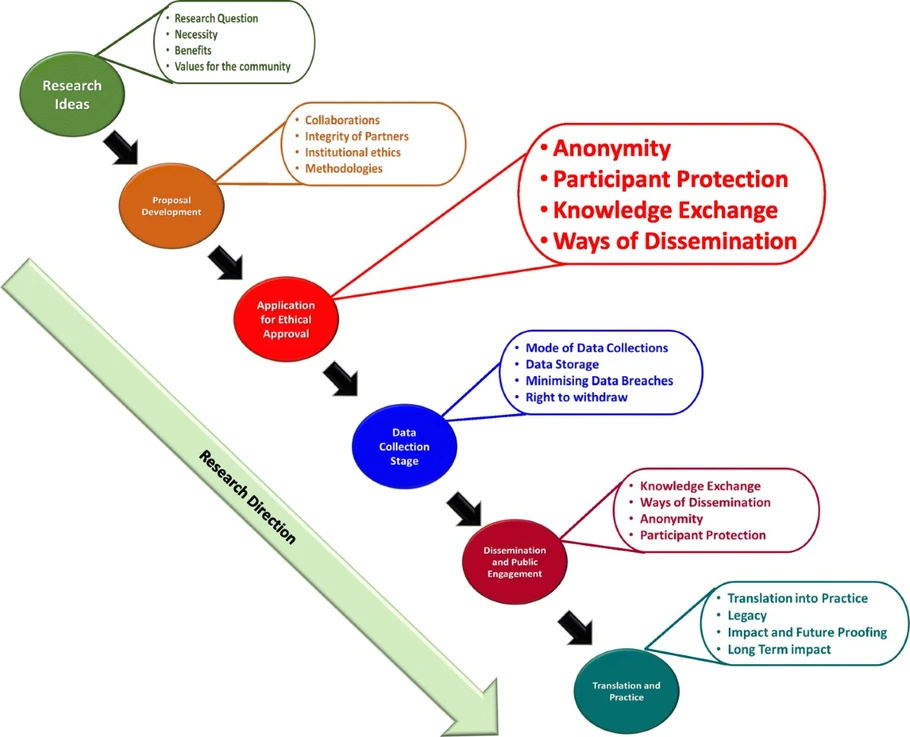
Figure 4: Pre-test Activity
(Source : https://edintegrity.biomedcentral.com/articles/10.1007/s40979-021-00078-6)
Ethical Steps Before Conducting a Test
However, to conduct a penetration test, the ethical hackers are supposed to adhere to a legal and systematic approach to prevent the violation of privacy of the organization that has hired them.
- Obtain Written Authorization: In order to undertake the hacking test, the ethical hacker requires to obtain prior written consent from the company. This also makes certain that the test is legal and that one is not liable to be taken under the false premise that he is tapping into a system to which he has no right.
- Scope of Engagement: It should be explained what systems must be incorporated into the test and how to prevent potential interferences (Ambalavanan et al., 2020). This involves ascertaining which resources are out of bound to reduce risk exposure that is likely to be incurred.
- Non-Disclosure Agreement (NDA): The client often requires the ethical hacker to sign a non-disclosure agreement as a condition of service provision. It bars the disclosure of some information with the company’s property and its businesses to third parties hence preserving the company’s reputation.
- Risk mitigation : ethical hackers should assess and evaluate the risk factors which may be likely to occur in the course of the testing such as disruptions, data loss and down time. Measures should be taken in anticipation of occurrences that have the potential of creating havoc in the society/organization.
- Communication Plan: Effective communication channels help in clearing the ideas and approaches of the testing process with the stakeholders. This would include everyday updates and as soon as possible reporting of the vulnerabilities, so that the company can take the necessary measures as soon as possible.
Taking the following ethical measures, penetration testers make sure such security tests are efficient, legal, and useful for the organization, enhancing the company’s security level.
Reference list
Ambalavanan, V., 2020. Cyber threats detection and mitigation using machine learning. In Handbook of research on machine and deep learning applications for cyber security (pp. 132-149). IGI Global.
Activity 2.5: Ethical Hacking Process
Solution:
Common Ethical Hacking Processes
- Footprinting : It is the process of obtaining preliminary information on the target end such as the domain names, their IP address and open ports using tools such as Nmap and domain/IP address WHOIS (Jaquet-Chiffelle et al., 2020). This helps identify potential vulnerabilities.
- Exploitation : ethical hackers take advantage of the acquired information to penetrate the system’s network. The most common attack strategies which can be used to infiltrate the network are the SQL injections, cross-site scripting (XSS), and brute force to attain unauthorized access.
- Post exploitation : Following gaining access, ethical hackers take over the control of the target system and attempt to become a system administrator to know the amount of harm an attacker could cause in case he or she gains such access.
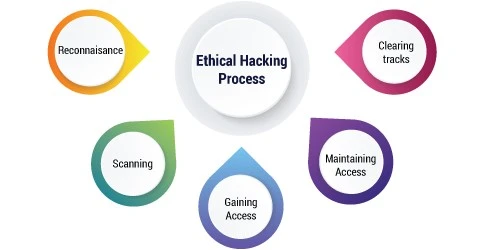
Figure 5: Ethical Hacking Process
(Source : https://www.invensislearning.com/blog/phases-of-ethical-hacking//)
Stages Involved in Digital Forensics
- Acquisition: Collects and preserves potential proofs in computers, networks, mobile devices for further examination.
- Preservation: Items are written protected and images are taken to prevent data modification and data duplication is done to ensure that the evidence is valid.
- Verification: Digital forensic also involves an authentication process where the collected data is hashed to ensure that no changes were made.
In this way, the ethical hackers and forensic specialists positively identify, take advantage of, and protect the weaknesses that make the security strong and stable.
Reference List
Jaquet-Chiffelle, D.O. and Loi, M., 2020. Ethical and unethical hacking. The ethics of cybersecurity, pp.179-204.
Activity 2.6: Forensic Tools
Solution:
Forensic Tools for Data Acquisition
Computer forensics tools are used for acquiring data/evidence, maintaining the integrity of the evidence, investigation and providing authentication in computer crimes. These tools help to maintain evidential credibility of the collected forensics and its admissibility in the court (Hawamleh et al., 2020). The following are the three main forensic tools that are used for implementing the field of cybersecurity:
- Autopsy: A tool that is particularly used in the investigation of digital systems and devices through retrieval of evidential data. This makes it possible to regain deleted files, review file systems as well as pick data from disk images.
- Nmap: Scanner that is very frequently used in penetration testing and sometimes even in digital forensics(Ghosh et al., 2020). It assists in determining which ports are open, which services are currently running and which network weaknesses are existent to be exploited in a cyber attack.
- FTK Imager: A software which allows the creation of forensic images of hard drives or other removable storage media. it provides an advantage of data preservation as the files are not changed in the course of storing the evidence.
Figure 6: Forensic Tools
(Source : https://www.jaroeducation.com/blog/digital-forensics-tools-and-techniques/)
Case 1: Using Autopsy for File Recovery
An incident in a company involves the insider threat where an employee erased some data belonging to the firm before leaving the organization (George et al., 2023). This is usually done by investigators through using what is known as Autopsy to see the deleted files erased from the laptop’s hard drive belonging to the employee.
Steps:
- Obtain Data: In this process, the investigator uses a tool to make a duplicate copy of the hard drive or sometimes referred to as imaging.
- Keep Data: A write blocker ensures that any data within the drive is protected from being overwritten in one way or the other.
- Check handedness: Autopsy analyzes the copies obtained from the forensic picture and restores files, logs, and browsing history, which prove that the employee copied information to an external hard drive then deleted it.
Case 2: Using Nmap for Network Analysis
A university does not alert and possibly infested by an unauthorized access that indicates it has been attacked. The team investigating the matter employs Nmap as a tool to scan through the network to check for weaknesses.
Steps:
- Gather Information: After identifying hosts of interest on the university network, an investigator will execute Nmap scans to discover the ports and services opened up on the organization’s servers.
- Security: This means that all scanner results are recorded and stored with the time stamps so that they may be used for investigations.
- Check: In the scanning outcome, the investigators found out that there is an unpatched server having a vulnerable weak structure of SSH enabling intruders’ access (Hu et al., 2020).More details from the crime scene investigation therefore suggest that a wrong-end-of-the-stick was on this loophole to sneak into students' records.
Some of the main products to work with digital evidence include Autopsy, Nmap, and FTK Imager in gaining possession, preserving, and evaluating the credibility of the acquired evidence. They help cybersecurity specialists to recognize invasions, the risk factors that may lead to them and control threats. Thus, the proper usage of forensic procedures helps to allow only the appropriate evidence to be collected and submitted in court, while retaining its credibility to be of use for investigations.
Reference List
George, A.S. and Sagayarajan, S., 2023. Securing cloud application infrastructure: understanding the penetration testing challenges of IaaS, PaaS, and SaaS environments. Partners Universal International Research Journal, 2(1), pp.24-34.
Ghosh, E. and Das, B., 2020. A study on the issue of blockchain’s energy consumption. In Proceedings of International Ethical Hacking Conference 2019: eHaCON 2019, Kolkata, India (pp. 63-75). Springer Singapore.
Hawamleh, A.M.A., Alorfi, A.S.M., Al-Gasawneh, J.A. and Al-Rawashdeh, G., 2020. Cyber security and ethical hacking: The importance of protecting user data. Solid State Technology, 63(5), pp.7894-7899.
Hu, Z., Beuran, R. and Tan, Y., 2020, September. Automated penetration testing using deep reinforcement learning. In 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW) (pp. 2-10). IEEE.
Conclusion
In today’s world, there are many threats that act against unauthorized access to data, that is why ethical hacking and digital forensics are used. Ethical hacking can be defined as the activity that aims at the assessment of certain systems, networks or applications with the intention of uncovering flaws that are likely to be exploited by hackers. That is why it involves such methods as White Box Testing, Grey Box Testing, and Black Box Testing to offer an all-round evaluation of security.Penetration testing is an important aspect of cybersecurity as it involves imitation of an actual attack. Red Team as the team that will seek to pretend to attack and breach the system in a manner that the Blue Team will have to protect by patching and detecting intrusions, and encrypting loops. Moreover, the software patching can help especially when it comes to issues like ransom-ware to reach a particular status of system security.Digital forensic deals with acquisition, examination as well as analysis of digital evidence involving elements of an incident pertaining to the nature of digital forensics as a sub-discipline of computer science; tools such as Autopsy, Nmap and FTK Imager were used in accessing and analyzing the materials.
This write-up is only a sample, and a fully customised version can elevate your assignment to a far higher academic standard. Ethical hacking tasks often require deeper critical analysis, clearer comparisons, accurate technical explanations, and well-structured academic writing to meet grading criteria. If you need a refined, original, and personalised version—aligned with your module outcomes, writing style, and expected depth—Native Assignment Help can create a polished, academically sound piece tailored specifically for your submission. Just specify your level and requirements, and we’ll produce a professional, assessment-ready version.
Reference list
Journals
Ambalavanan, V., 2020. Cyber threats detection and mitigation using machine learning. In Handbook of research on machine and deep learning applications for cyber security (pp. 132-149). IGI Global.
Baddam, P.R., 2020. Cyber Sentinel Chronicles: Navigating Ethical Hacking's Role in Fortifying Digital Security. Asian Journal of Humanity, Art and Literature, 7(2), pp.147-158.
Christen, M., Gordijn, B. and Loi, M., 2020. The ethics of cybersecurity (p. 384). Springer Nature.
Conteh, N.Y. and Schmick, P.J., 2021. Cybersecurity risks, vulnerabilities, and countermeasures to prevent social engineering attacks. In Ethical hacking techniques and countermeasures for cybercrime prevention (pp. 19-31). IGI Global.
Devi, R.S. and Kumar, M.M., 2020, June. Testing for security weakness of web applications using ethical hacking. In 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI)(48184) (pp. 354-361). IEEE.
Dhirani, L.L., Mukhtiar, N., Chowdhry, B.S. and Newe, T., 2023. Ethical dilemmas and privacy issues in emerging technologies: A review. Sensors, 23(3), p.1151.
George, A.S. and Sagayarajan, S., 2023. Securing cloud application infrastructure: understanding the penetration testing challenges of IaaS, PaaS, and SaaS environments. Partners Universal International Research Journal, 2(1), pp.24-34.
Ghosh, E. and Das, B., 2020. A study on the issue of blockchain’s energy consumption. In Proceedings of International Ethical Hacking Conference 2019: eHaCON 2019, Kolkata, India (pp. 63-75). Springer Singapore.
Hawamleh, A.M.A., Alorfi, A.S.M., Al-Gasawneh, J.A. and Al-Rawashdeh, G., 2020. Cyber security and ethical hacking: The importance of protecting user data. Solid State Technology, 63(5), pp.7894-7899.
Hu, Z., Beuran, R. and Tan, Y., 2020, September. Automated penetration testing using deep reinforcement learning. In 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW) (pp. 2-10). IEEE.
Jaquet-Chiffelle, D.O. and Loi, M., 2020. Ethical and unethical hacking. The ethics of cybersecurity, pp.179-204.
Sridhar, K. and Ng, M., 2021. Hacking for good: Leveraging HackerOne data to develop an economic model of Bug Bounties. Journal of Cybersecurity, 7(1), p.tyab007.